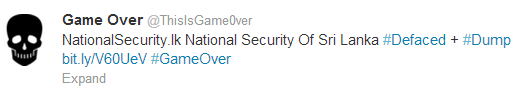
The Sri Lankan Media Center for National Security (nationalsecurity.lk) has been broken into and defaced by a hacker operating under the name “Game Over”. This post first came to our attention via a third-party link on the United State of Geeks Facebook page.
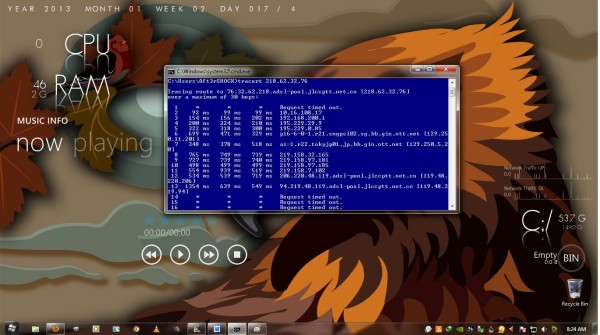
According to the bulletin reports, Game Over did not just break into the site: for a while nationalsecurity.lk redirected to lovefcc.com/gameover before the site was taken down for maintenance. In addition, the hacker also broke into the server, dumped the database to an archive and leaked the login credentials of a large number of users. Hundreds of email addresses and passwords are still available in the form of a text file posted online (http://218.62.32.76/releases/nationalsecurity.txt). The database dump is presumably unavailable for access right now. A basic and IP lookup run from my PC shows that file residing on a server in Changchun, China.
|
IP Host: |
76.32.62.218.adsl-pool.jlccptt.net.cn |
|
Continent: |
Asia (AS) |
|
Country: |
China (CN) |
|
State: |
Jilin |
|
City: |
Changchun |
|
ISP: |
CHINANET YunNan PROVINCE NETWORK |
|
Organization: |
China Unicom Jilin province network |
|
Time zone: |
Asia/Harbin |
|
Continent Lat/Lon: |
29.8405 / 89.296 |
|
Country Lat/Lon: |
35 / 105 |
|
City Lat/Lon: |
(43.88) / (125.3228) |
|
IP Language: |
Standard Chinese (Mandarin/Putonghua), Yue (Cantonese), Wu (Shanghaiese), Minbei (Fuzhou), Minnan (Hokkien-Taiwanese), Xiang, Gan, Hakka dialects, minority languages
|
This isn’t Game Over’s first profilic hack: HackRead reports that Game Over struck at Pakistan’s Okara police force site previously, which leads us to believe that this hacker could be operating in the South-East Asian region. Either that, or he/she is practicing for more secure sites.
The Media Centre for National Security (MCNS) is no small site. It was established for the specific purpose of pushing out national security related information to the media and public from one central location; it is the official centrepoint for media coordinators working with the three armed forces, Police and the STF into the bargain.
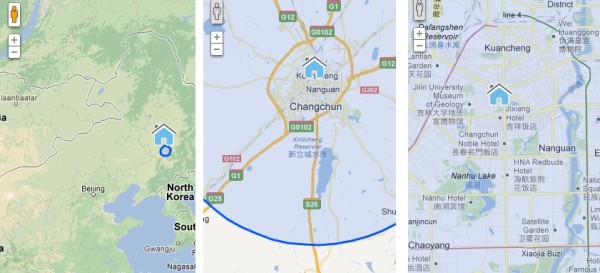
This is the data server’s location highlighted in a series of Google Maps. Worse than the login leak is that database dump, which Game Over linked to in his document (http://www.nationalsecurity.lk/MCNS/defence-security/news/backup/db_backup.2013-01-14.sql.gz). Any number of hackers and/or activists could have that data right now. At this point the Department of Defense is limited to damage control: either they have to shut down the site and rebuild from scratch, or they have to persuade the Government of China to take that file off that server. Either way, the damage is done. MCNS is compromised.
The ugly truth is that, this was clearly substandard online protection. This sort of data is too sensitive to be placed in what is clearly an archive of substandard protection. Game Over could have incited a nation-wide panic by pulling the right strings. The Government either needs to realize the dangers of putting up everything on the ‘net – or hire better developers.







small question, what is the OS u are running?? Is that a custom theme u are using????