April 2022 has been an unforgiving month for Sri Lanka’s digital space with attacks ranging from government website takedowns to compromised user data being leaked online. One of the more notable on the list is the PayHere hack. On April 1, Bhasha’s fintech arm PayHere was breached and the service went offline for 36 hours before coming back online. Amidst the PayHere hack, the company stated that no card details have been compromised since these details are stored in the partner bank’s PCI DSS certified servers (Sampath Bank and Seylan Bank).
A month after the attack, PayHere published a detailed statement with regard to the incident. However, questions still remain on the service’s safety and what it all means for users.
What was compromised in the PayHere hack
PayHere first launched its operations back in 2016 as a user-friendly payment gateway solution for Sri Lanka. Although the service quickly gained popularity it was shortly shut down three months later due to legal challenges over the “Payment & Settlement Systems Act”. However, PayHere returned in 2017, partnering up with Sampath Bank. Since then, the service has been growing strong. In fact, by November 2021, it crossed LKR 5 billion in total transactions processed. Now, amidst this growing success, the company has fallen victim to what appears to be one of Sri Lanka’s biggest data breaches.
On April 1, PayHere confirmed that the service was under a cyber attack including its SMS gateway. 36 hours later in a Facebook post, the company stated that services were back online and that payments were getting processed as usual. The post also mentioned that the attacker wasn’t a local party and that international traffic was blocked as a precaution.
At the time, assurance was given that no credit card details have been compromised as PayHere doesn’t store card details on company servers. Rather, these details are processed on Sampath Bank and Seylan Bank’s ends. These banks are partnered up with Paycorp and UnionPay which is PCI DSS certified (PayHere’s PCI DSS compliance is achieved via proxy). Nevertheless, the severity of the attack remains alarming.
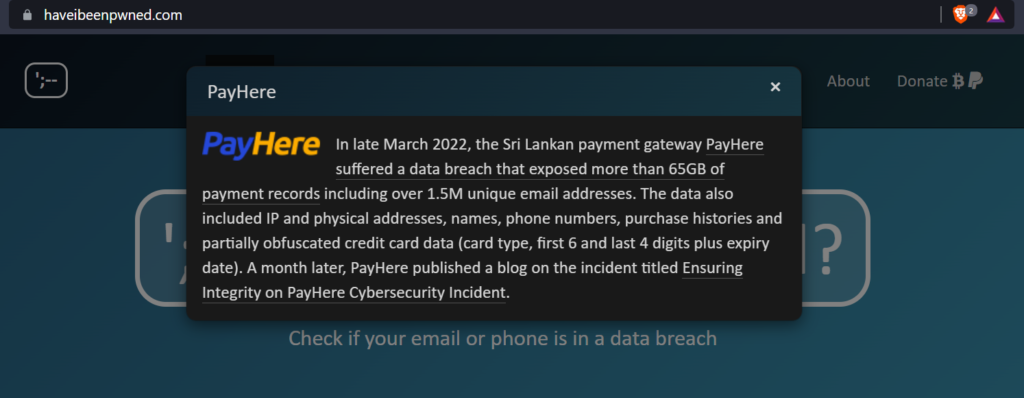
According to Have I Been Pwnd, the PayHere hack exposed over 1.5 million payment records or more accurately 1,580,249. The 65GB worth of exposed data includes IP and physical addresses, names, phone numbers, purchase histories, and partially obfuscated credit card data (card type, first 6 and last 4 digits plus expiry date). This is in contrast to PayHere’s claims that no credit card details were compromised.
PayHere’s response
When it comes to onboarding merchants to PayHere, the service does so through a paperless mechanism. Part of this includes uploading the relevant documents online. In response to the attack, PayHere claims that it suspects this is how the attacker might have comprised the service, through a malware-planted file upload. The company claims that it’s currently working with SL CERT “to find out the exact root cause of the attack.” Until then, PayHere won’t be onboarding new merchants to its service.
Further, PayHere states that it took steps to change all of its 3rd-party payment integration credentials and the merchant credentials. “We regenerated the domain-specific Merchant Secrets of our merchants and communicated the new credentials to be updated from their side. We also reset the Merchant Portal Passwords immediately and requested the merchants to set new passwords to the Merchant Portal,” the statement reads.
The attacker had also allegedly planted a webhook to get alerts on new user logins after the attack that would store user passwords in plaintext. Following this, PayHere has reportedly informed affected merchants about the possible risk, in addition to resetting merchant portal passwords from the company side.
PayHere states that it has shut down the compromised server and has now moved to a new distributed infrastructure. Additionally, the company mentions several other security measures,
- Strict firewall rules
- Geographical restrictions
- Rate limiting
- Change of shared credentials (details shared between PayHere, payment processors, and merchants)
- Complete source code analysis and vulnerability assessments on PayHere systems, review of the overall security of PayHere services via cyber security firm
By April 3, PayHere restored its Payment and Payout Processing System following a security review. At the time of writing, the company’s Merchant Portal is yet to be restored fully and is only to be done so after a full security review according to PayHere.
What now?
By now, PayHere has reported the incident to Sri Lanka Police’s Cyber Crime Investigation Division and the CCID has reportedly started investigations. The company is also looking into the possibility of any legal action provisioned by the Computer Crime Act and the Personal Data Protection Act in Sri Lanka. As far as how well this pans out for PayHere, only time will tell.
But PayHere’s response with regard to the incident has been lackluster at best. After all, over 1.5 million records have been compromised and it took the company a month to offer a detailed response. Even then, there has been no communication on the 1.5 million records that were compromised as a result of the PayHere hack. When one inquired about the company’s failure to report this, PayHere responded stating that it had legal advice not to publish the detailed report “as it may benefit the criminal.” Although common sense dictates following such an incident, informing users should be the first on the list.
Troy Hunt, the creator of Have I Been Pwnd, says that the breached data made his multiple times more than two weeks ago. In other words, the data is already in the public domain leaving the risk of data falling into wrong hands all the same, if not worse. As Hunt puts it, “it’s easier when the victims don’t know they’ve been breached.”
With regard to card data, PayHere mentions that no card details have been compromised. However, in actual reality, the PayHere hack also gained access to partial credit card data including the card type, first 6 and last 4 digits plus expiry date. As history shows, even partial details can still give you away.
So if you’re one of PayHere’s many customers or someone who has just used the services before, now would be a good time to change all your important passwords. Make sure you have two-factor authentication enabled on your email accounts that you’ve used to access PayHere services. We would also encourage you to use a reliable password manager (if you don’t already) and start using strong passwords while avoiding the same passwords for multiple accounts. It’s not foolproof, but it’s a good start to keeping your online presence safe.
As for PayHere, the company states that the CCID is currently investigating the incident and that updates will be shared once more details come to light. We will update this article should that be the case.





GIPHY App Key not set. Please check settings