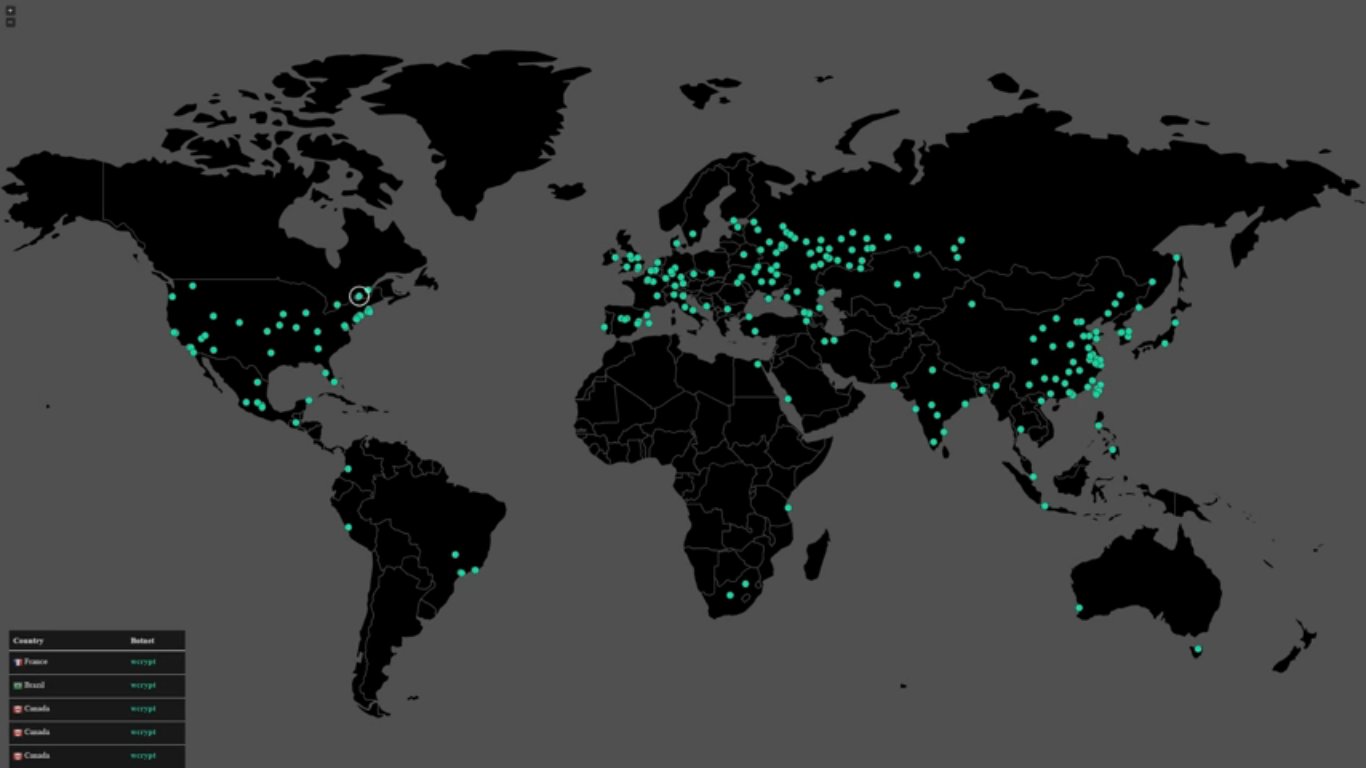
In a recent worldwide cyber attack, a ransomware program that goes by the name WannaCry has managed to infect computers from all over the world. Reports claim that 99 countries were affected by WannaCry, including China and Russia. Among the severely affected were the UK’s National Health Service(NHS) and Spain’s Telefonica, along with a number of businesses around the world. According to BBC, about 40 NHS organizations were impacted by the ransomware, causing hospitals to be closed down and operations to be canceled. Even our neighboring country, India looks to have taken a hit. However, there seem to be no reports of WannaCry incidents from Sri Lanka so far.
What Does WannaCry Do Exactly And How Did This Happen?
As you would expect with ransomware, the victim’s computer files will be locked and encrypted. The only way one could gain access again is to pay whatever demanding ransom. After which you would be able to decrypt these encrypted files. With WannaCry, the demand is $300 in bitcoin. Once affected, a pop-up window would appear with instructions on how to make the payment. This pop-up also features 2 clocks. One clock would display the 3-day deadline to pay the ransom. Once reached, the demand amount doubles. The second clock shows a deadline when the victim would lose their data forever.
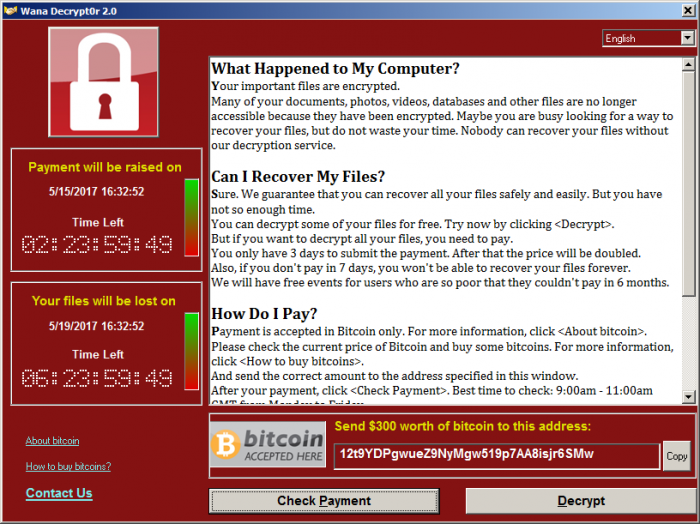
Usually, ransomware relies on humans for it to get into computers. However, it looks like WannaCry looks is spreading via a worm. This essentially spreads by itself between computers within a network.
It is believed that a group of hackers calling themselves ShadowBrokers are behind the attack. This seems to use an exploit of a Windows Software vulnerability. Dubbed ETERNALBLUE, the exploit was developed by the National Security Agency(NSA). The same group had released this exploit last month, along with a collection of spy tools that were allegedly used by the NSA. Although Microsoft already patched this vulnerability, it looks like those affected were the ones who haven’t updated their software to get this fix.
WannaCry Kill Switch: An Accident Might Have Saved You
Following the massive crisis, a malware analysis expert who goes by MalwareTech examined WannaCry. What he accidentally found was a kill switch that stopped the ransomware from spreading further. Unfortunately, this did not impact any of the already affected systems. However, this is only temporary though. MalwareTech’s solution may have slowed down the ransomware. But this does not mean WannaCry is gone and out. In fact, all that’s needed is for the attackers to change the code and start again.
Should I Be Worried? What Should I Do?
Most of us use the internet on a daily basis. So ransomware of this magnitude should obviously be of serious concern to all of us. Microsoft even rolled out an update to its older operating systems such as the Windows Server 2003, Windows XP, and Windows 8, despite the fact that the company no longer provides mainstream support for them. Thankfully, people are already working on a permanent fix for the issue. But does this mean you have nothing to worry about? Not quite. Here are a few things you should do to keep yourself safe from these types of harmful attacks.
- Keep your Operating Systems updated. Yes, this can be annoying sometimes, but it’s absolutely vital (as we’ve clearly seen).
- Always keep your anti-virus program and other software up to date
- Maintain a regular backup of your important files. For instance, you could get an external hard drive and keep a copy of your files on it.
- Have a pop-up blocker running on your web browser
- Most importantly, DO NOT click links, attachments, or emails from people you don’t know. This is true for a lot of cyber attacks, not only ransomware.
As far as we know, WannaCry hasn’t made it to Sri Lanka, let’s hope the situation remains the same. There are also rumors of WannaCry 2.0, a new version of the ransomware without the kill switch. However, there’s nothing official on this as of yet. We’ll be sure to update this post should anything come up. Until then, stay safe.
Update
As of now, the number of affected victims has risen to around 200,000 in at least 150 countries. Rumors of a WannaCry 2.0 may look to be a little more than just a rumor now. According to The Hacker News, Costin Raiu from the global research and analysis team at Kaspersky Labs confirmed to had seen WannaCry samples without the kill switch. So unless the vulnerable systems are patched, chances are this might make another round, and this time the damage might be more serious.





Instead of blocking popups we can block js on browsers and regular backups will be useful. And wannacry 2.0 is not a rumour. 🙂 😀
Best regards
It was at the time of writing. Will update should anything new come up. Thanks for the comment 🙂
Just turned on the Automatic updates..and baam my data limit reached. 🙁
Ah :/ that damn data! Hope you have off peak data left on your package though 😀
Only automatic updates will not help. Actually if you are enterprice level user, IT teams might already taken necessary measures, but a a end user
Do not open e any email which is from unknown sender
Do not open any email which is not expected
Do know open any email with attachment,links which is unexpected but from know sender
If anything is suspicuose ,unsure hit the delete button.
It would be Better be crefull.this really a disaster and could not stop if end users are not supportive to the Corp IT Team
I think the statement about the “ShadowBrokers” is incorrect. They found the heap of tools which was being used by NSA and published them to the public with source codes and usages data. Probably someone else who learned about this stash had used them to extort money with WannaCry ransomeware….
Would using a Apple Mac system be a safer way to go?? not a expert just a Question…
Yup. Mac and Linux are always safer options.