Ah yes. Security. The one thing everyone forgets about until you notice those unfamiliar purchases on your eBay account. Of course, the past few years have seen the tech industry take a little more interest in cybersecurity. Several local universities and education institutes already have specializations in the field. But even so, security is a very serious problem. One could say it’s probably a bigger threat today than it was 5-6 years ago. The dawn of IoT, AI, big data, and the like would probably be one reason.
As such, the folks at SLASSCOM put together a hands-on session, titled, “Application Security and Beyond”, which was conducted by Nirosh Jayaratnam – Senior Security Engineer at 99x Technology.
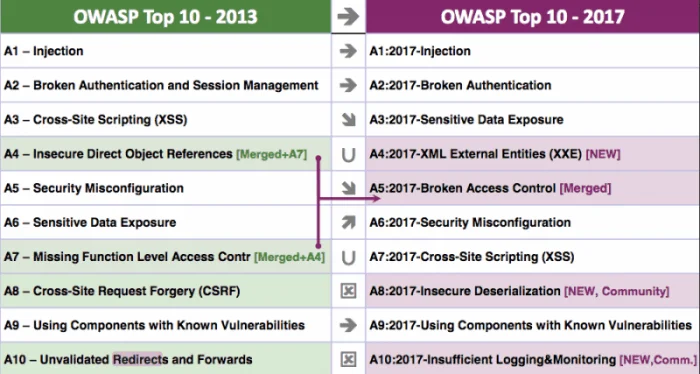
As the title suggests, the focus was on application security. The majority of the session looked at specific types of vulnerabilities with reference to OWASP’s list of web application-related risks.
SQL Injection
If you take a web application for example, each of them is connected to a database. In case you’re not a techie, these databases usually communicate in a language called SQL. In a scenario when the databases aren’t properly protected, web applications can pose certain vulnerabilities. These vulnerabilities are exploited via SQL injection.
So how exactly do these SQL injections happen? Well, there are quite a few ways. But for the most part, a textbox is all it takes, where user input is requested. Imagine a website that requires you to log in. An instance of SQL injection would see an input like ’12 OR 1=’1’’ or something similar is entered as a login entry. What would happen here is that this input would become part of the original SQL query and unknowingly run on your database. Before you know it, the intruder gains access without even having proper login credentials.
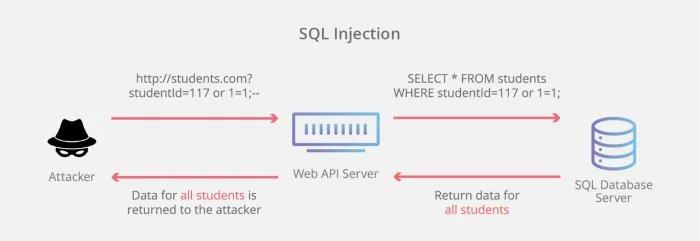
As stated before, there are few ways SQL injection attacks can occur. The above was one of them. In case you’re still thinking “what can this actually do to me”, the impacts of such attacks could vary from impersonating users to deleting records from databases.
So how does one protect themselves from SQL injection? One way is to include prepared SQL statements with parameterized queries. Stored procedures and Input validation are a couple of others. In the case of open forms, reCAPTCHA would serve well. For a detailed look at these methods, you can head over here.
Broken Access Control
This is when a web application’s access control or authorization, is incorrectly configured. The danger here is that such a vulnerability could pave the way for attackers to gain access to sensitive data, or even bring down the website.

There are a few ways to tell if your authorization schema can be bypassed.
- Can an unauthenticated user access a particular resource?
- Can a resource be accessed even after logging out?
- Can certain functions and/or resources be accessed by a user who holds a different role or privilege?
Protecting yourself from these types of attacks would require you to pay attention to insecure ID’s, path traversal, client-side caching, file permissions, and forced browsing past access control checks.
Cross-Site Scripting (XSS)
This is also another injection type of attack. This is usually when a malicious code is sent from an attacker to another user via a web application. As per OWASP, Cross Site Scripting can occur “anywhere a web application uses input from a user within the output it generates without validating or encoding it.”
XSS attacks usually fall under 2 categories, stored XSS attacks and reflected XSS attacks. Stored attacks refer to when the malicious script is permanently stored in the target servers. Reflected attacks are ones that get reflected off a web server. These usually take the form of error messages, search results, etc. But if you want to understand XSS attacks in general, there’s actually a pretty good local case study.
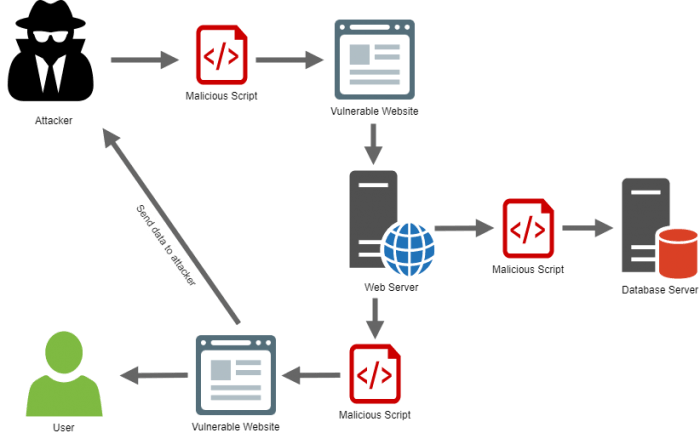
Identifying XSS-related vulnerabilities can sometimes be challenging. If you’re a developer, there’s an OWASP XSS prevention cheat sheet you can refer to.
More attention toward security
Of course, these are only a few of the web application security risks that occur on a daily basis around the world. As Nirosh Jayaratnam – Senior Security Engineer at 99x Technology. puts it, 95% of web applications today have some sort of vulnerability. In Sri Lanka, that’s not so hard to believe considering how “secure” some of our websites are.
While beefing up security when it comes to websites and web applications comes under the responsibility of the developers, there’s also a fair share of responsibility that falls under the other stakeholders as well. Sometimes it can be as simple as using a secure password. On that note, if you do actually want to double-check how secure your password really is, you can do so here.
Unfortunately, even in 2019, security isn’t given the proper attention it’s supposed to be given by the society at large, at least in a Sri Lankan context. But more workshops like these is definitely encouraging. One can hope these discussions in the tech community would eventually get translated to the rest of the general populace. Until then, we all have our work cut out for us.







GIPHY App Key not set. Please check settings