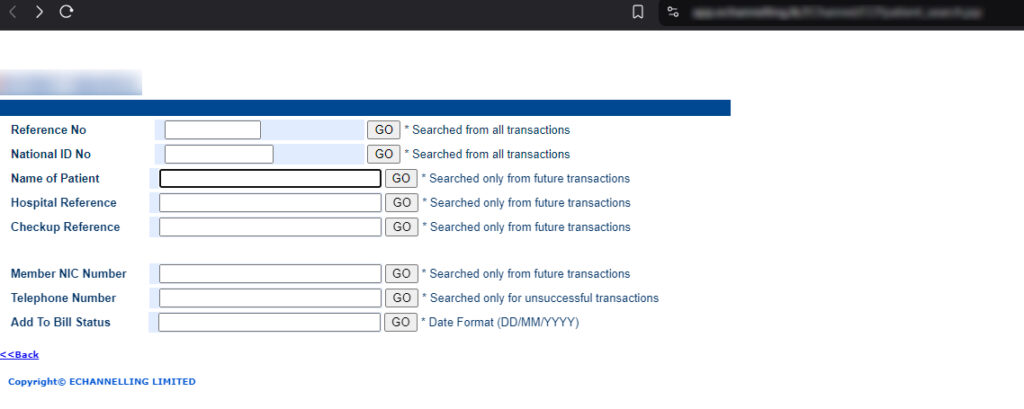
Mobitel’s eChannelling website hosted a search page that exposed sensitive patient data. Initially spotted by a Reddit user, the publicly accessible page allowed anyone with access to find patient details such as name, National ID, phone number, and other personal details with a simple name search.
The page was shortly taken down following the Reddit post. However, it’s unknown how long this page has been publicly accessible. Given that the platform hosts over 260 hospitals and 5,500 doctors, at least tens of thousands of user data may have been potentially compromised.
eChannelling incident response
It’s also unclear what prompted the specific page to be left open. The company claims that it conducts three internal security audits (SLT and Mobitel) and three external assessments via TechCert annually. As per eChannelling’s reporting, its IT infrastructure and security are handled by a two-man engineering team. The overall IT security infrastructure falls under the purview of the Mobitel Data Center.
As part of a typical incident response plan (see SLCERT guideline) over a cyber security incident, an organization would immediately patch the vulnerability and verify security. This is followed by notifying all concerned parties. In eChannelling’s case, this pertains to customers, hospitals, and doctors who may be immediately affected. The disclosure would also include the likes of SL CERT and law enforcement as potentially breached data includes personally identifiable information associated with a health service.
However, the vulnerability was left unaddressed until a public Reddit post. At the time of writing, neither Mobitel nor eChannelling disclosed the data leak.
Protective measures for concerned users
One possible action is to contact the company directly at [email protected] and request that it not process personal information any further. The eChannelling site doesn’t specify any processes regarding cyber security incidents. But it does explicitly point out that customers can reach out via its general email regarding the company’s privacy practices.
Further, users could also get in touch with SL CERT by email at [email protected], the 101 hotline, or directly on the website.

Worrying signs
Quantifying the exact impact of this data leak is challenging. Unlike a typical breach, there isn’t a dataset circulating online that indicates the potential severity of the situation. However, this incident could pose issues for eChannelling, considering the scale of its services and user base. Only time will tell whether this results in something less or more consequential than an increase in spam and smishing texts.
Further, the incident adds to a worrying trend of cyber attacks in Sri Lanka. From PayHere and SLBFE to allegedly PickMe and Aviation Services, reports of data breaches are becoming a regular occurrence. This is amplified by Sri Lanka still falling short on regulatory protection for data privacy violations.
Drawing a straight line between a data breach and its repercussions may be precarious. The lack of user protection only widens this gap. But it should raise the alarm to enable better data protection mechanisms, particularly state-owned institutes that offer access to critical health services.
Lagging regulations
Incidentally, the Personal Data Protection Act (PDPA) accounts for this type of scenario. Unfortunately, in its current standing, the Act could only be enacted once the Data Protection Agency is appointed. Earlier this year, the government stated that the agency is expected to be operational by 2025. A recent gazette announced that the Data Protection Agency will come under the Ministry of Digital Economy – the president’s purview.
Sri Lanka also has a Cyber Security Act that’s been in the works over the past few years. The proposed Act aims to enact cybersecurity-related guidelines via institutes like SL CERT. Much like the PDPA, this Act will be followed by the setting up of the Cyber Security Authority. “From the part of law enforcement, I admit that we do not have the strongest mechanisms and tools to deal with cyber criminals and dispense justice to victims effectively,” stated Public Security Ministry Secretary Ravi Seneviratne at a recent cyber security event.
Unfortunately, until the Government of Sri Lanka’s digitalization efforts encompass cyber security and data privacy in equal weight as its other initiatives, incidents like eChannelling’s data leak will be a continuing trend. At the very least, prompting better security safeguards for critical services should not be reliant on publicized social media posts.
Update 29/11/2024: Added context regarding the company’s incident response and potential contact points for concerned users






GIPHY App Key not set. Please check settings