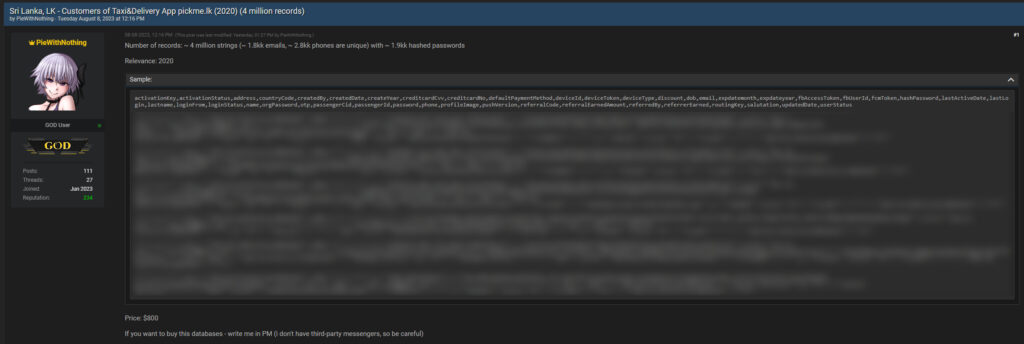
Recently, we reported about a possible data breach at PickMe where a leaker under the pseudonym PieWithNothing claimed to be in possession of 4 million PickMe customer records. The company refuted any implication of the supposed leak and that it had “investigated such claims thoroughly and have ruled out the alleged data breach.” PickMe went on to clarify specifics around its data handling and security in a detailed statement. However, more recent revelations cast serious data privacy and security concerns for the general citizenry.
Barely two days after our story went live, the alleged leaker updated the initial post to include three new entries as sample data (six users in total), complete with details such as name, email, phone number, and hashed passwords. After a preliminary inspection, we were able to confirm the validity of the sample, at least in terms of the specified names, emails, and phone numbers. While this doesn’t mean that four million records have been compromised, or that PickMe itself is involved, it does point to a possible breach at some level.
Responding to a query on how six user details were publicly disclosed by the leaker, PickMe refuted claims of any breach on the company’s end. Adding further, PickMe CMO Mohan Gamage mentioned that “during service transactions, certain customer information is made available to users such as merchants and agents via the platform for legitimate and mutually agreed purposes under and in terms of our user agreements.” He also specified that “there are also, unfortunately, plenty of independent means and ways to collect and collate additional information on individuals that is publicly available online. Using such publicly available information, a lookalike data set can be created to paint the picture of a breach.”
What we know so far
Notably, the published sample data includes hashed passwords of the six users. While PickMe moved away from passwords to OTPs a few years ago, it’s worth noting that the exposed passwords still pose risks to users. This is because most people tend to use the same password for many of their online accounts for different services. So there’s a real danger that someone could easily gain access to some of your other accounts, especially if there’s no two-factor authentication or similar protection in place. In fact, during our own inspection, we were able to decrypt two of the six passwords. A more skilled, malicious actor could potentially translate to much bigger implications.
Other sensitive information like card details is a different story. Standard practice would mean users’ card details are only retained within PickMe in tokenized form. In other words, even in the case of a breach at PickMe, your card details are obfuscated. In fact, even the leaker claimed that the supposed 4 million-string dataset has this field, but is empty.
Interestingly, this isn’t the first time for PieWithNothing when it comes to putting up compromised databases for sale. Whether it’s selling the data of Lebanese car owners (3 million records) or an Indonesia-based delivery service (20 million records), PieWithNothing comes with a notorious history, typically selling databases for around $500 – $700. One 2022 report from cybersecurity company Fortinet even marks PieWithNothing as a credible threat actor. So if PieWithNothing’s history is anything to go by, it’s that there’s very real concern about the possibility of a data breach as opposed to some random attempt at discrediting a Lankan tech company. However, as to where the data came from remains unanswered.
Personal Data Protection Act
Regardless of the PickMe side of the equation, the PieWithNothing incident points to a much bigger problem in Sri Lanka. For instance, how did this data get out in the first place? The fact there’s a dataset of personal information of six people available in a public forum should raise enough alarm bells by itself. But, even as entire chunks of government databases get leaked onto the internet and scammers run rampant across the island, the general response has often been lackluster.
Fortunately, Sri Lanka now has its own Personal Data Protection Act (PDPA) in effect. However, its overseeing body the Data Protection Authority (DPA) is yet to be fully operational. This means that matters pertaining to the PDPA such as developing guidelines, investigating complaints, imposing penalties, and raising awareness are yet to be incorporated into practice.
Specifically, clause 12 (1)(b) of the PDPA states that a company should have “a mechanism to receive complaints, conduct of inquiries and to identify personal data breaches.” and that any breach should be reported to the DPA (clause 23 (1)). Although, the actual enactment of any of these provisions in the PDPA seems to be in limbo in its current form.
The DPA itself is expected to be fully functional by 2024 and it expects to meet the Act’s enforcement 19 March 2025 deadline. However, it should be pointed out that much of this depends on how much emphasis the current government will place on the DPA, particularly around its budgetary allocations and other vital resources. As to how the PDPA can help citizens and corporate entities right now, remains another question unanswered.
Calls for better transparency
Of course, PickMe’s own response hasn’t exactly garnered confidence in offering technical assurance. The company did refute and offer disclaimers on concerns related to credit card information and passwords. Though, a post-incident review followed by proactive messaging could have translated to better goodwill. It certainly doesn’t help that the typical tendencies of corporate entities often lean toward reactive damage-control responses as opposed to proactively notifying users of any potential incident. Bhasha’s PayHere is an apt example here.
Back in 2022, PayHere suffered a massive data breach that exposed over 1.5 million records. While the company’s initial response did little to inspire confidence, PayHere’s eventual improved communication topped with its post-incident handling process prompted a positive turn of events for the company. In the months that followed, PayHere would file a complaint with the Cyber Crime Investigation Division of Sri Lanka Police as well as work with a cybersecurity firm for a security audit. Additionally, Sri Lanka CERT would go on to publish a report on the incident.
It’s important to note that no company is unhackable in today’s digital space. Whether it’s the 1.11 petabytes of Uber data getting compromised or Okta’s hack leaving over 17,000 corporate entities vulnerable, cyber security incidents are part and parcel of an organization with an online infrastructure. But if PayHere’s approach is anything to go by, it’s that proactiveness and transparency can go a long way. In contrast, the general response to security concerns/incidents showcases the need for a better corporate culture around cybersecurity. At least as far as accountability and transparency are concerned.
Right now, there’s a public online forum with the personal data of six Sri Lankans with a known threat actor alleging to have compromised a Lankan tech company. So far, the response hasn’t gone beyond a corporate rebuttal from the company itself. But as to who will answer the lingering questions on the broader data privacy implications, only time will tell.






GIPHY App Key not set. Please check settings